Introduction
The digital age has made our lives easier in many ways, offering convenience, efficiency, and connectivity like never before. However, it has also created new threats, especially with regards to our personal information. Hackers, those with malicious intent and technical expertise, can exploit vulnerabilities in our online activities to gain unauthorized access to our sensitive data. In this tutorial, we will explore the various methods hackers use to obtain personal information and ways to protect ourselves.
Phishing Attacks: The Art of Deception

Phishing attacks are among the most common techniques used by hackers to obtain personal information. In this type of attack, hackers create deceptive emails, text messages, or even phone calls that appear legitimate to trick individuals into revealing their sensitive information, such as passwords or credit card details. They often pose as trusted entities, such as banks or online services, and employ psychological techniques to lure victims into divulging their data.It is crucial to remain vigilant and cautious when dealing with such communications. Be skeptical of unsolicited messages that request personal information or urge immediate action. Always verify the authenticity of the source using official channels before providing any sensitive data.
Malware: The Silent Invader

Malware, short for malicious software, is another weapon employed by hackers to compromise our digital security. Malware can infect our devices through various means, including downloading files or clicking on infected links. Once installed, it can perform a multitude of malicious activities, such as stealing personal information, recording keystrokes, or even taking control of the entire system.To protect ourselves from malware, it is essential to employ robust cybersecurity measures. These include installing reputable antivirus software, regularly updating operating systems and applications, and being cautious while downloading files or clicking on suspicious links.
Brute Force Attacks: Breaking Down Barriers
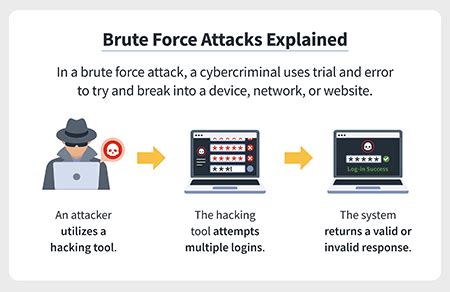
Brute force attacks are a method hackers employ to crack passwords and gain unauthorized access to systems or accounts. This method involves repeatedly trying different combinations of characters until the correct password is discovered. Hackers often use automated software that can rapidly generate and test thousands of password combinations within seconds.To protect against brute force attacks, it is vital to use strong and unique passwords for each account. A strong password includes a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, enabling multi-factor authentication, which provides an extra layer of security, can significantly reduce the risk of a successful brute force attack.
Wi-Fi Eavesdropping: Snooping on the Unsecured
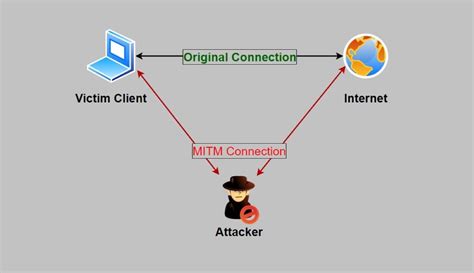
Wi-Fi eavesdropping, also known as "sniffing," involves intercepting and capturing wireless network traffic to gather sensitive information. Hackers can exploit the vulnerabilities present in insecure Wi-Fi networks, such as those without encryption or weak security protocols, to monitor users' online activities and steal their data.To protect against Wi-Fi eavesdropping, it is crucial to utilize secure Wi-Fi networks encrypted with WPA2 or WPA3 protocols. Avoid connecting to public Wi-Fi networks unless absolutely necessary, as they are often insecure and prime targets for hackers. Additionally, using a virtual private network (VPN) can provide an added layer of encryption and security while browsing the internet.
Social Engineering: Manipulating the Human Element
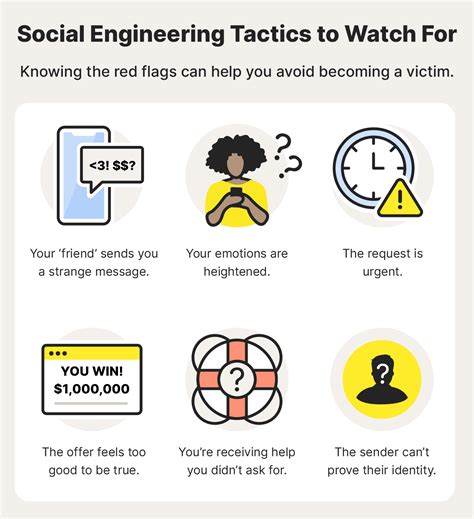
Social engineering is a form of psychological manipulation that aims to exploit human trust and naivety for nefarious purposes. Hackers utilize various techniques, such as impersonating trusted individuals, creating urgency, or offering false incentives, to trick individuals into divulging their personal information or granting them unauthorized access to systems.Protecting against social engineering attacks starts with education and awareness. Be cautious of sharing sensitive information with unknown entities and verify the authenticity of requests through independent channels. Avoid clicking on suspicious links or downloading files from untrusted sources. By developing a skeptical mindset, we can significantly reduce the risk of falling victim to social engineering tactics.
Conclusion
In this tutorial, we have explored some of the common methods employed by hackers to obtain personal information. By understanding these techniques, we can take proactive steps to protect ourselves. Practicing good cybersecurity habits, such as being cautious of phishing attempts, using strong passwords, staying aware of Wi-Fi security, and being wary of social engineering tactics, can go a long way in safeguarding our personal information. Remember, vigilance and continuous learning are essential to stay one step ahead in the ongoing battle against hackers.
No comments:
Post a Comment